
Cybersecurity
Microsoft Teams, The New Target of Cybercriminals
22 September 2023
Microsoft Teams has become a pillar of professional communication and collaboration, enabling teams to work together effectively, whether in the office or remotely. However, like any popular technology, Microsoft Teams is not immune to vulnerabilities and security threats. Microsoft recently published a report regarding cyberattacks carried out against Microsoft Team by exploiting social engineering to deceive users and distribute malware.
One of these vulnerabilities, dubbed “Midnight Blizzard,” deserves special attention. In this article, we’ll explore this phenomenon and how you can protect your business.
How does this new type of attack work?
These new attack methods against Microsoft Teams aim to deceive user vigilance and bypass the protection mechanisms put in place in your Azure or Microsoft 365 organization.
Malicious actors use compromised accounts from businesses to launch their attacks. By modifying the name and domain of compromised accounts, they pretend to be a Microsoft service such as “Microsoft Identity Protection” in order to fool users. A communication request is then sent to the user, if they accept, the attacker then tries to convince them to enter a code in the Authenticator application in order to bypass Multi-Factor Authentication (MFA)
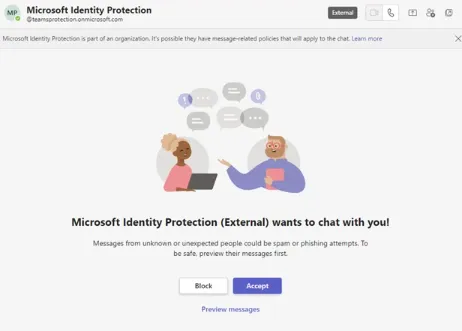
Step 1:
An external communication request is routed using a trusted pseudonym, in this example the request appears to come from the Microsoft Identity Protection Service. A user may be fooled by the legitimate appearance of this request if they do not pay attention to the red indicators in this image.
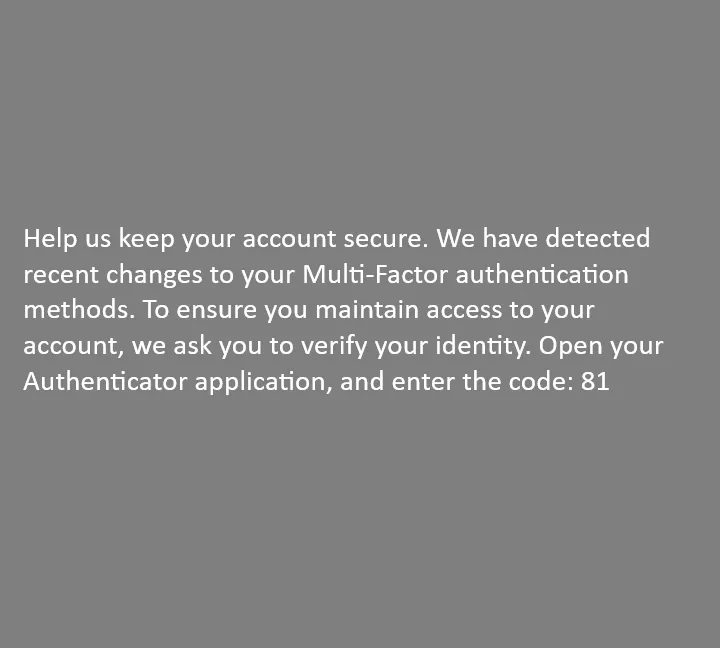
Step 2:
If the user accepts the conversation, the attacker will attempt to gain access to the account by bypassing Multi-Factor Authentication (MFA) methods. To achieve this, the attacker simply needs to enter a code into the targeted user’s Microsoft Authenticator application, which will allow them to gain full control of the user’s Microsoft account.
To deceive the user, a message is displayed suggesting recent changes to their account authentication methods and that they must confirm their identity.
Features included in Microsoft Teams to protect you
- Explicit request: End users do not see messages unless they click to preview them, users are reminded of the risks of external chat and are asked to explicitly accept or block the message request.
External - Identifiy: Visible in both the discussion list and the discussion header.
- Spam Checks: Prior to explicit “opt-in,” every message sent from a Teams personal account is subject to run-time spam checks. If spam is detected, the chat message is not sent.
- User Security: To help protect the user, Microsoft only displays the name and email address, but no other identifiers like profile photos.
The majority of these measures allow users to detect the validity of a Teams conversation via certain criteria. What about incidents that are not detected or simply not reported by users?
Using Microsoft Intune and Microsoft Sentinel can significantly strengthen the security of your Teams, SharePoint, and Azure environment. Here are the advantages of these solutions:
Microsoft Intune :
Device management: Intune lets you manage the devices used to access Teams. You can apply security policies to devices to ensure they comply with security standards. Only authorized devices have access to your data.
Access control: Use Intune to configure access control policies, including managing access rights to data and applications on devices. Reduce the attack surface by limiting the geographic areas that have access to your data.
App configuration: You can configure Teams app configuration policies to define specific security settings, such as Multi-Factor Authentication (MFA) for Teams and Azure.
Securing data: Intune lets you encrypt data on devices to prevent unauthorized access.
Update management: Ensure devices used to access Teams are always up to date with the latest security patches by setting up update management policies.
Microsoft Sentinel:
Advanced monitoring: Microsoft Sentinel is a security event management (SIEM) solution that allows you to monitor activities in your Teams, Azure and Office 365 environment in real time. Microsoft Sentinel allows you to detect potential threats, alert your security teams and automatically trigger protection measures based on the type of threat.
Threat detection: Configure threat detection rules in Sentinel to monitor suspicious behavior, abnormal login activities, and indicators of compromise related to Teams, Azure, and Office365.
Incident response: Create automated workflows in Sentinel to quickly respond to security incidents related to Teams, Azure and Office365, such as quarantining a compromised user.
Integration with Teams: Microsoft Sentinel can be integrated with Teams, Azure, and Office365 to collect activity logs and other security data. This allows comprehensive monitoring of your Microsoft cloud environment.
Security Reports: Use Sentinel to generate custom security reports and to maintain an overview of the security of your Teams, Azure and Office365 environment.
The combination of Microsoft Intune and Microsoft Sentinel provides in-depth management and monitoring of your Microsoft cloud solution, strengthening the overall security of the platform. It is essential to configure these services properly, monitor activities closely, and respond promptly to any potential threats to keep your data secure.

